Knowledge Byte: Threat Model for Cloud Service Deployment

Cloud Credential Council (CCC)

Each service and deployment model has its own risks. The best way to treat risks within cloud is to develop a threat model for the service deployment based on the assets in cloud.
What is a Threat Model?
- A model of the system (cloud environment), which depicts:
- The system structure, its components, and the flow of control relationships.
- The assets (data and function) in the system.
- The security controls protecting the assets.
- This model of the system is compared against:
- A list of potential ‘threat or risk scenarios.’
- A list of potential attackers, disasters, (natural or man-made), and human error.
Threat Modeling in the Cloud
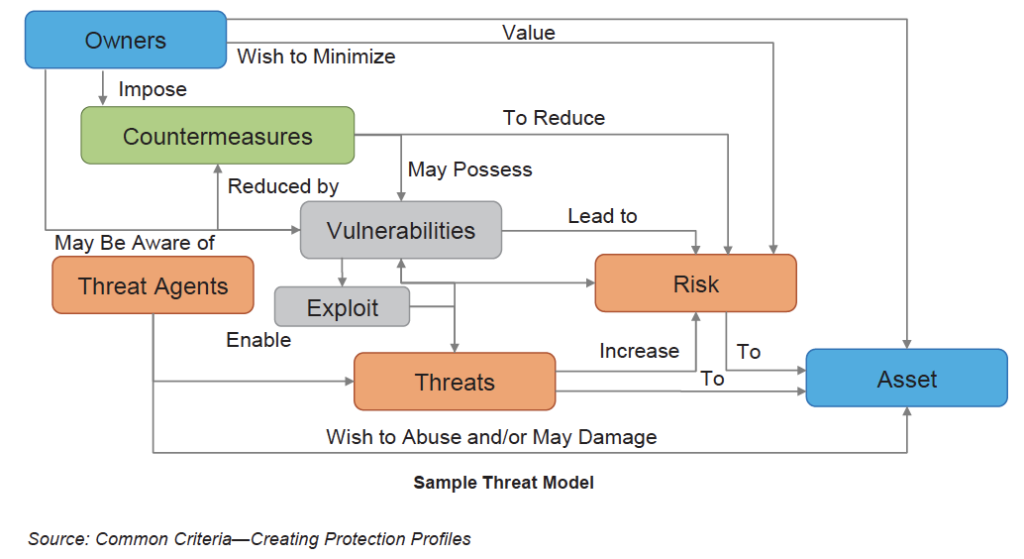
The objective of the threat model is to identify and assess threats in a cloud service. It involves examining the assets, vulnerabilities, entry points, and actors in the cloud environment.
The threat model shows that everything starts with an owner and ends with an asset. Organizations moving into the cloud need to understand their business ownership and the value of their asset in order to apply appropriate countermeasures or protections. The following figure shows a sample threat model:
Courses to help you get
results with Cloud
Professional Cloud Security Manager Certification
The industry-recognized CCC Professional Cloud Security Manager provides you a case study with related exercises and activities such as multiple-choice questions (MCQs), multiple MCQs, puzzles, and write-ups. This case study will focus on security and risk considerations that should be considered while implementing cloud computing in small and mediums organizations. We made sure to include…
Never miss an interesting article
Get our latest news, tutorials, guides, tips & deals delivered to your inbox.
Keep learning




